Author: Roy Samson
This article defines a reference architecture for an integrated (privileged) access management system through describing the following elements in this realm:
- Security functions;
- Technical capabilities;
- Open source software solutions;
- Open (source) security protocols;
- Security architecture principles;
- (Privileged) access management component roles;
- Security design pattern.
From a function point-of-view the system most provide the following services:
- Access management services, defined as functionality for providing an access method -such as a gateway- for users to resources;
- Identification, authentication, authorization, and single sign-on services;
- Access governance services, defined as functionality for administrating identities, accounts, authorizations, and permissions.
These functionalities translate to the following selection of technical capabilities:
- A reverse proxy solution;
- An identity provider solution for identity authentication purpose;
- A strong authentication solution;
- Single sign-on solution;
- A privileged access and account management system;
- Secure storage of access credentials;
- An identity and access management solution.
Open source software available for building such a solution, respectively:
- Nginx Proxy Manager (https://nginxproxymanager.com/);
- OpenLDAP (https://www.openldap.org/);
- LinOTP (https://linotp.org/);
- Apero Central Authentication Service (CAS) (https://www.apereo.org/projects/cas);
- Apache Guacamole (https://guacamole.apache.org/);
- SoftHSM (https://www.opendnssec.org/softhsm/);
- OpenIAM, KeyCloak, Apache Syncope (https://www.openiam.com/ ,https://www.keycloak.org/, https://syncope.apache.org/).
Relevant open (source) security protocols in the (privileged) access management realm:
- OpenID providing authentication (https://openid.net/);
- Oath providing strong authentication (https://auth0.com/);
- Oauth is an open authorization protocol (https://oauth.net/);
- XACML (eXtensible Access Control Markup Language) is an XML-based standard markup language for specifying access control policies (http://xml.coverpages.org/xacml.html);
- SAML an open standard for exchanging authentication and authorization data (https://wiki.oasis-open.org/security/FrontPage);
- OASIS a standard -XML-based framework- for creating and exchanging security information between online entities (https://www.oasis-open.org/).
Security architecture principles in the realm of (privileged) access management:
- Need-to-know;
- Need-to-use;
- Segregation-of-duties;
- Least privilege;
- Zero-trust.
To illustrate the purposes of the different components in the (privileged) access management realm often the following roles are used:
- A Policy Enforcement Point (PEP) assures the enforcement of the policy;
- A Policy Decision Point (PDP) collects information from one or more PIP’s, assesses this based on policy rules, to come to a policy decision;
- A Policy Information Point (PIP) contains information attributes relevant for a policy decision;
- A Policy Administration Point (PAP) administrates identities, accounts, authorizations, permissions, and policy rules.
A simple security design pattern in the realm of (privileged) access management looks as follow:
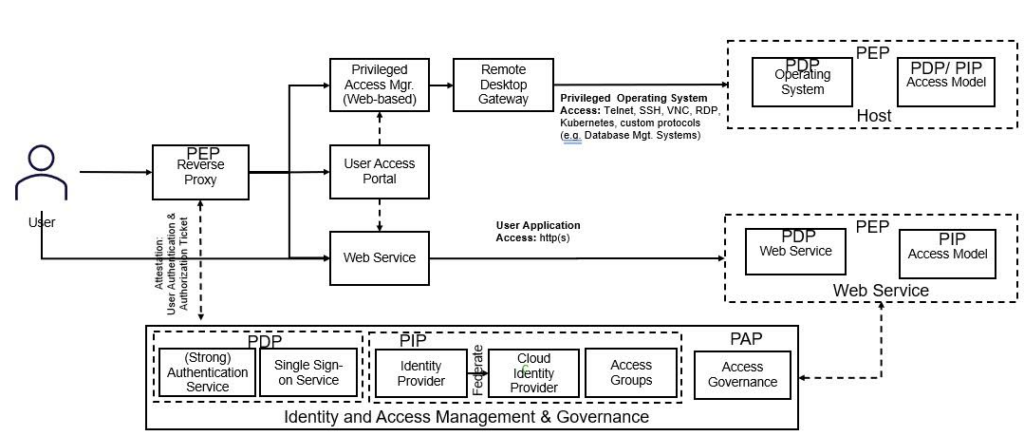
The role of the first PEP in above design patterns is to enforce whether a user is allowed to access a service yes or no. The role of the second PEP in above design patterns is to enforce what a user is allowed within the service.